ISARA Insights Blog

Is Your Cryptographic Infrastructure Healthy?
What about your organization’s cryptographic infrastructure? Is it healthy? What can enterprises do now to keep theirs in good shape, especially as the industry collectively moves toward post-quantum cryptography? With enterprises planning the migration of their entire cryptographic assets from classical…
Tags:

Is Your Cryptographic Infrastructure Healthy?
What about your organization’s cryptographic infrastructure? Is it healthy? What can enterprises do now to keep theirs in good shape, especially as the industry collectively moves toward post-quantum cryptography? With enterprises planning the migration of their entire cryptographic assets from classical…

All Aboard the Quantum Migration Train
Standards bodies, government organizations, and research centers weigh in on preparing for the threat that quantum computers pose to encryption. Take action now? Don’t worry about it yet? Or, get on the quantum migration train now starting with planning and crypto-agility solutions?

Math Paths to Quantum-safe Security: Hash-based Cryptography
Digital signature algorithms are a critical component of public-key infrastructure, with applications ranging from code signing to establishing secure connections. However, classical digital signature algorithms will be vulnerable to quantum-enabled attacks. Hash-based cryptography is among the oldest…

ISARA Radiate™ Security Solution Suite 1.4 Brings XMSS to Complete its Offering of Stateful Hash-Based Signatures for Quantum-Safe Roots of Trust
With the latest release of the ISARA Radiate™ Security Solution Suite, we’ve added stateful hash-based signatures, specifically eXtended Merkle Signature Scheme (XMSS), to the cryptographic library. With this addition, we now offer complete stateful hash-based signature algorithm support. Also, using…
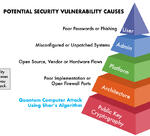
How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a surprise. There seems to be a new security breach almost every day; in January 2018 a bug was discovered…