ISARA Insights Blog
Tags:

Transforming PKI Migrations: Unlocking the Power of Crypto-Agility with Quantum-Safe Multiple Algorithm Certificates
Crypto-agility is the key to cost-effectively migrate information and communication technology (ICT) systems from legacy to quantum-safe systems. By using our unique dual algorithm approach to certificates, this is possible for large organizations and governments.

ISARA Radiate™ Security Solution Suite 1.4 Brings XMSS to Complete its Offering of Stateful Hash-Based Signatures for Quantum-Safe Roots of Trust
With the latest release of the ISARA Radiate™ Security Solution Suite, we’ve added stateful hash-based signatures, specifically eXtended Merkle Signature Scheme (XMSS), to the cryptographic library. With this addition, we now offer complete stateful hash-based signature algorithm support. Also, using…
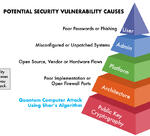
How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a surprise. There seems to be a new security breach almost every day; in January 2018 a bug was discovered…

Quantum Computing: Its Emergence & Implications on Information Security
Leading governments around the globe, along with major corporations, including IBM, Google, Microsoft, have all made substantial investments in the development of large-scale quantum computers, just in the past decade. There's a reason for this prescient obsession. What exactly is quantum computing? Quantum…

Why Quantum Computing is a Board Level Security Risk
In recent years, there has been an undisputed increase in enterprise data breaches across the globe. At first, this was only a concern for IT, CISO’s and CIO’s. However, with growing fiduciary responsibility, cybersecurity is gaining attention at board-level decisions. This is an important shift, as…